Microsoft’s Security Squad: A Zero Trust Party!
Table of contents
- The Zero Trust Breakdown
- 1. Multi-Factor Authentication (MFA): The Gatekeeper with Attitude
- 2. Microsoft Authenticator: Your Phone’s Cool Trick
- 3. Identity Protection: The AI Sleuth with Flair
- 4. Conditional Access: The Picky VIP List
- 5. Microsoft Entra ID: The Identity Rockstar
- 6. Microsoft Defender for Identity (MDI): The Retro Bodyguard
- 7. Microsoft Defender for Endpoint (MDE): The Device Dynamo
- 8. Privileged Identity Management (PIM): The VIP Pass Master
- Why I’m Hyped (and Microsoft’s My Dream Gig)
- Related Reading
Hey, tech pals! Imagine logins tougher than a locked treasure chest, devices that are your ride-or-die crew, and hackers bounced like party crashers. That’s Microsoft’s security squad and my big, goofy dream of joining their team.
The Zero Trust Breakdown
I’m spilling the tea on eight epic technologies that make Microsoft’s security magic happen:
Multi-Factor Authentication (MFA)
Microsoft Authenticator
Identity Protection
Conditional Access
Microsoft Entra ID
Defender for Identity (MDI)
Defender for Endpoint (MDE)
Privileged Identity Management (PIM)
We’re rocking Microsoft’s Zero Trust Framework with three killer principles:
Verify Explicitly
Use Least Privilege Access
Assume Breach
Or in human speak: “Check Everything, Give Just Enough, and Expect Trouble”
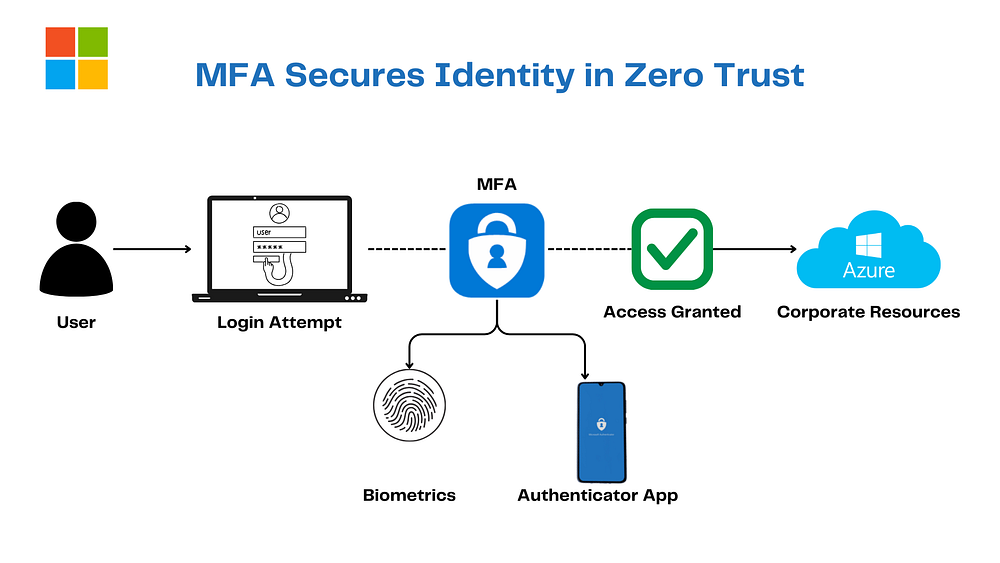
1. Multi-Factor Authentication (MFA): The Gatekeeper with Attitude
Passwords? Yawn. MFA’s the bouncer who’s all, “Prove it’s you twice, buddy!”
We’re talking:
Microsoft Authenticator pings
Windows Hello for Business
Temporary Access Pass
Biometrics
FIDO2 passkeys
Even a chill SMS
It’s tight with Microsoft Entra ID and gets sassy with Conditional Access to zap phishing and password spray attacks. In Zero Trust, it’s Verify Explicitly for the Identity pillar. No imposters crashing this party!
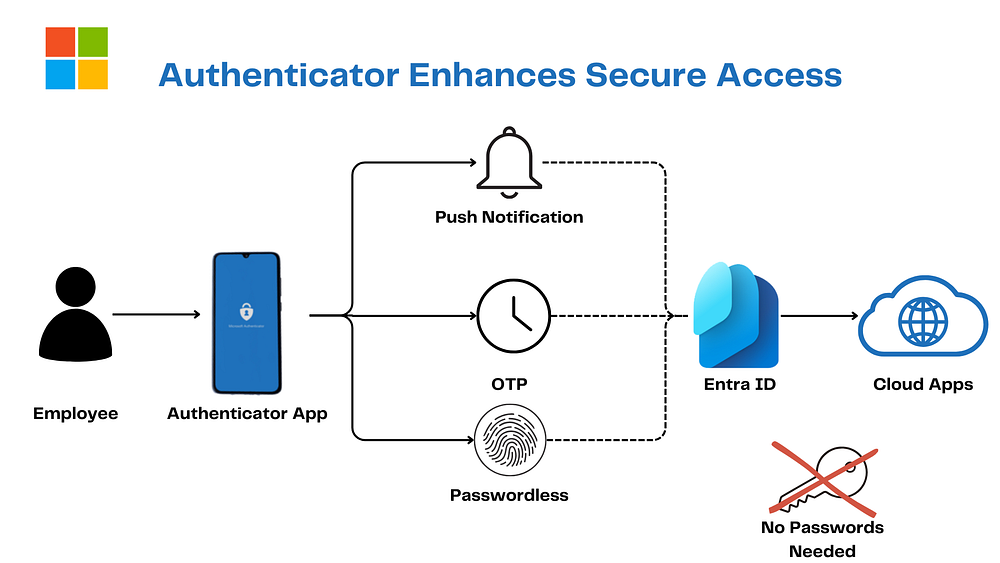
2. Microsoft Authenticator: Your Phone’s Cool Trick
Say what’s up to Microsoft Authenticator — your phone’s security DJ. It spins:
Push notifications
One-Time Passwords (OTPs)
Passwordless sign-ins with biometrics or FIDO2 standards
Hooked to Entra ID, it ditches lame SMS for phishing-proof jams. In Zero Trust, it’s Verify Explicitly for Identity, locking your login to a trusted device faster than you can say “cool beans.”
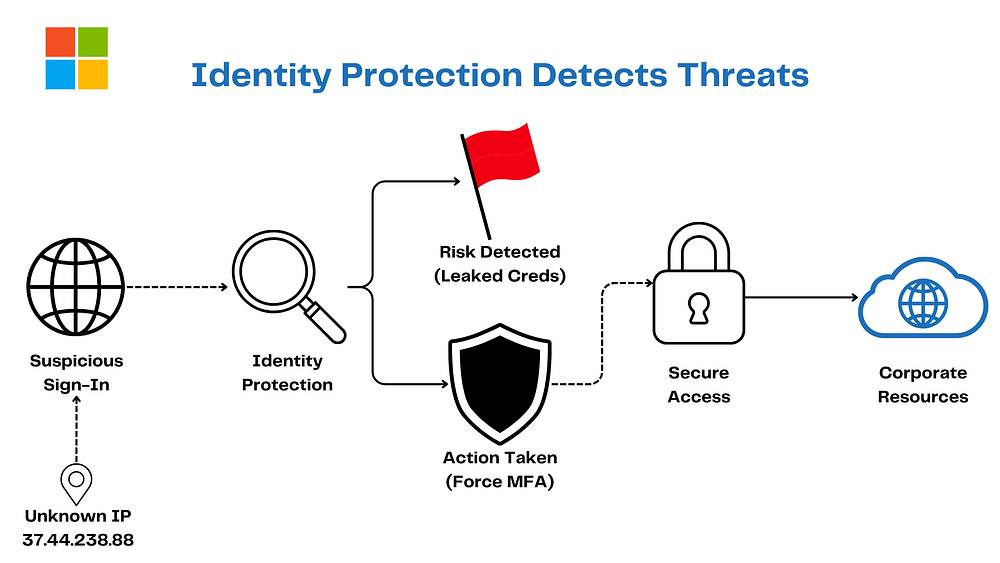
3. Identity Protection: The AI Sleuth with Flair
Who’s sneaking around your identity? Microsoft Entra ID Protection is the slick detective, sniffing out:
Leaked credentials
Sketchy sign-ins from malware-ville
With AI swagger, it throws risk scores and yells, “MFA time!” In Zero Trust, it’s Assume Breach for Identity, teaming with Conditional Access to kick trouble to the curb.
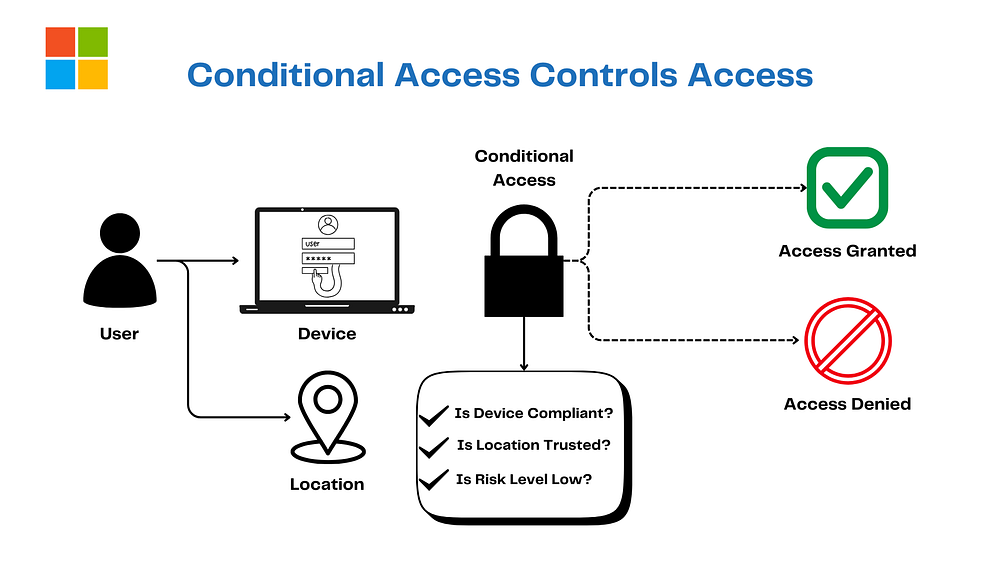
4. Conditional Access: The Picky VIP List
Conditional Access is the gatekeeper with a clipboard:
Device good?
Location chill?
Risk low?
It’s Entra ID’s policy rockstar, enforcing MFA or blocking shady logins on the fly. In Zero Trust, it’s Verify Explicitly and Use Least Privilege Access across Identity, Endpoints, and Apps. Only the VIPs get the green light!
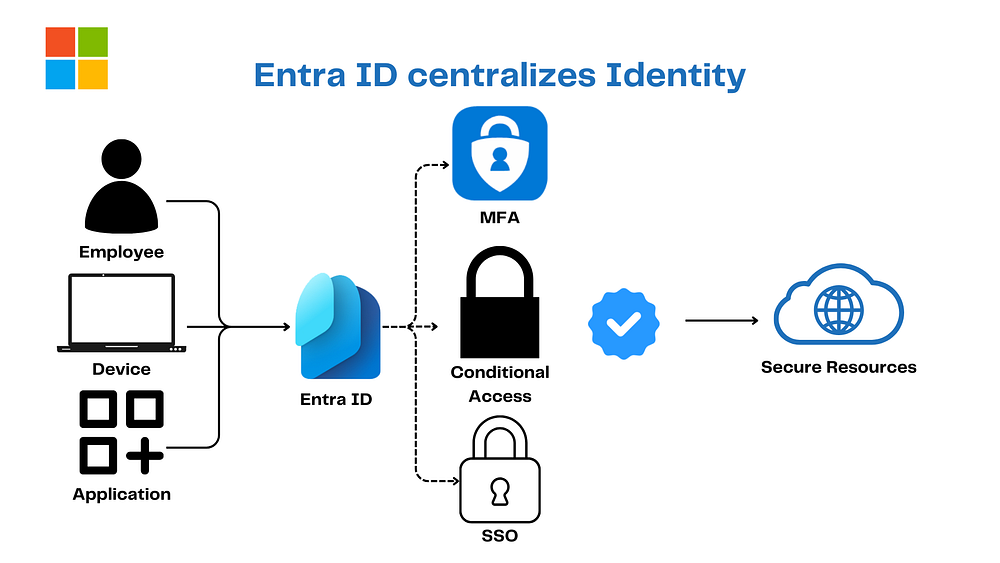
5. Microsoft Entra ID: The Identity Rockstar
Microsoft Entra ID’s the headliner a cloud-based Identity and Access Management (IAM) champ that runs:
Single Sign-On (SSO)
Multi-Factor Authentication
Conditional Access
Even works with hybrid setups! In Zero Trust, it’s the Identity pillar’s rockstar, nailing Verify Explicitly with strong authentication and Use Least Privilege Access via Role-Based Access Control (RBAC) and Privileged Identity Management (PIM).
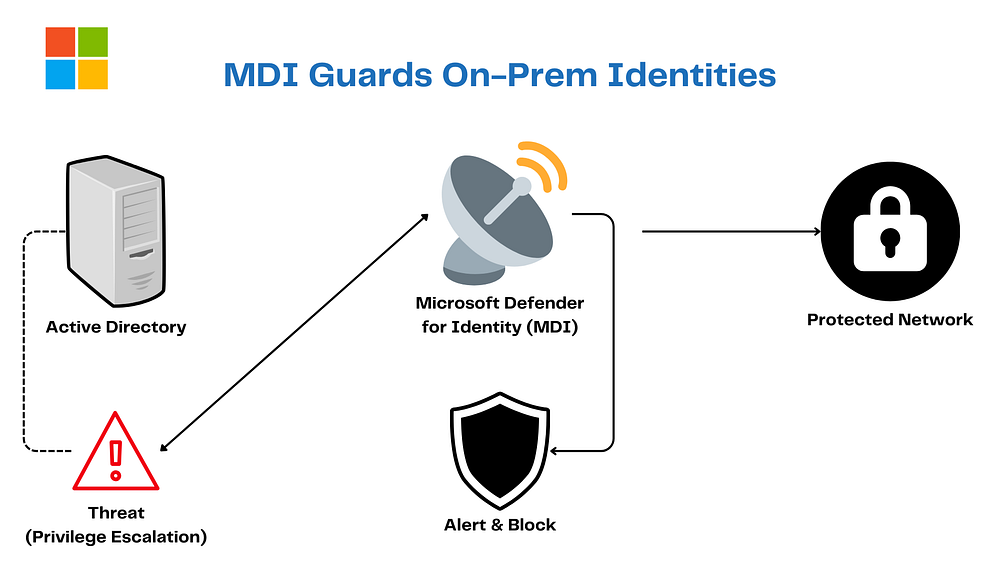
6. Microsoft Defender for Identity (MDI): The Retro Bodyguard
MDI’s the cool cat guarding your on-premises Active Directory. It catches:
Reconnaissance attempts
Lateral movement
Privilege escalation
With behavioral analytics and Microsoft Defender XDR integration, it’s Assume Breach for Identity and Infrastructure, keeping your old-school vibes safe and funky.
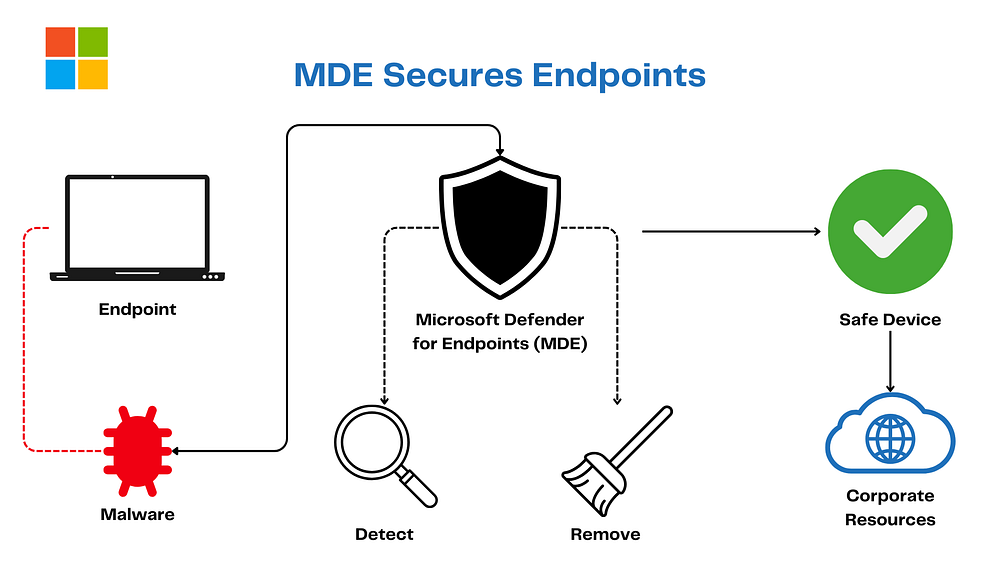
7. Microsoft Defender for Endpoint (MDE): The Device Dynamo
MDE’s the gadget guru, smashing:
Malware
Ransomware
Advanced Persistent Threats (APTs)
It syncs with Entra ID and Conditional Access to make sure your device isn’t a mess. In Zero Trust, it’s Assume Breach and Verify Explicitly for Endpoints your laptop’s got a superhero cape now!
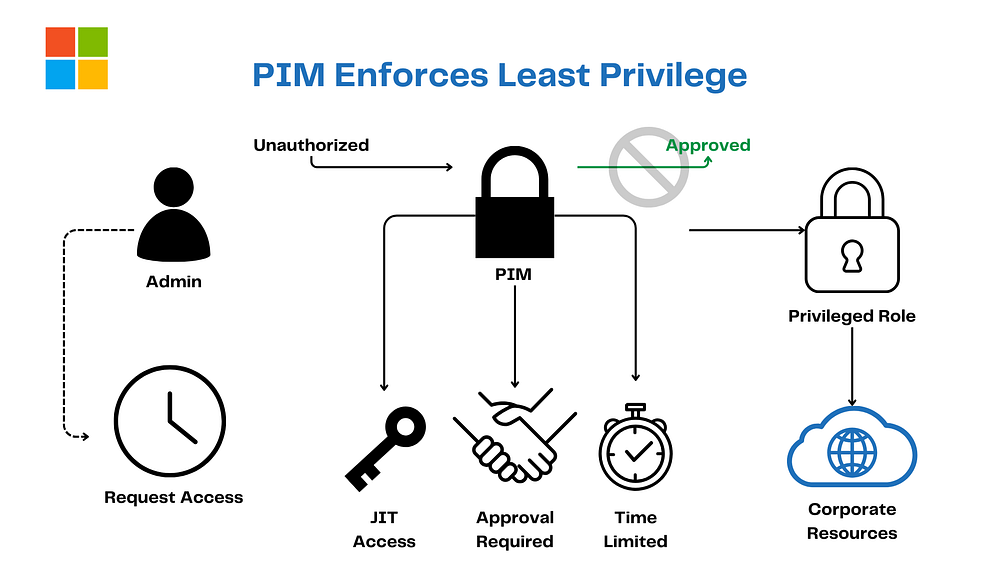
8. Privileged Identity Management (PIM): The VIP Pass Master
PIM’s the gatekeeper for the big shots. Nestled in Entra ID, it’s all “Want power? Beg for it!” with:
Just-in-time access
Approval requirements
Time-limited privileges
Comprehensive audits and alerts
In Zero Trust, it’s Use Least Privilege Access for Identity, keeping the VIP list short and the party tight.
Why I’m Hyped (and Microsoft’s My Dream Gig)
These tools aren’t just tech they’re a blast! Zero Trust is Microsoft’s secret sauce, mixing Verify Explicitly, Use Least Privilege Access, and Assume Breach into a security smoothie.
Microsoft squad, if you’re vibing with this: I’m a tech nerd with a big heart for your tools, itching to join the fun. Let’s make the internet a fortress hit me up!
Smack that clap if Zero Trust’s your jam too!